“There is no need to penetrate a network when you can breach the people who run it” – Unknown
Whoever said that is so right! Isn’t it? And this Phishing has become so common these days. Anyways here, I am going to show you another wonderful tool from my favorite Kali.
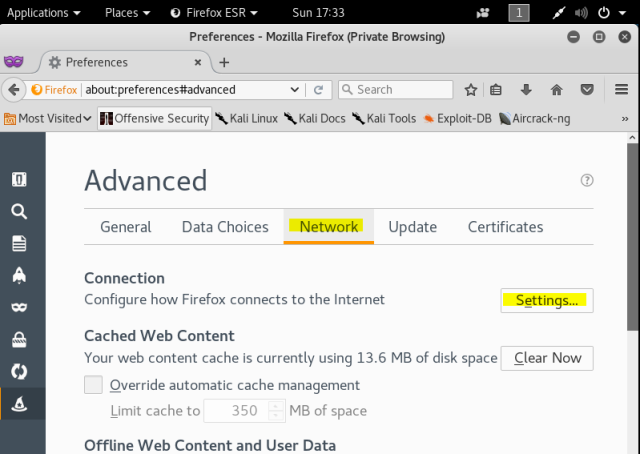
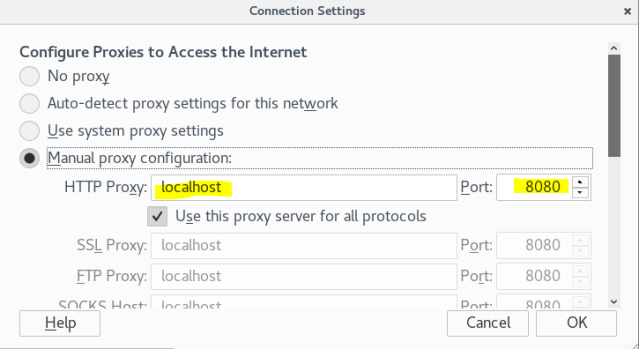
To launch this tool you can just type “setoolkit” in terminal or you can go to Application ->social engineering toolkit, which will take you the tool [as in screen shot 2]
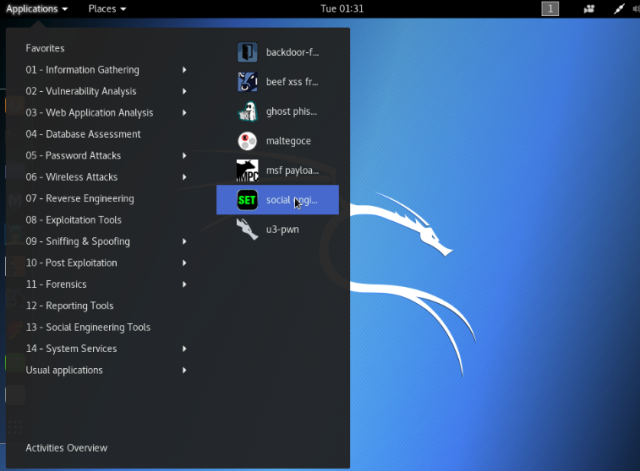
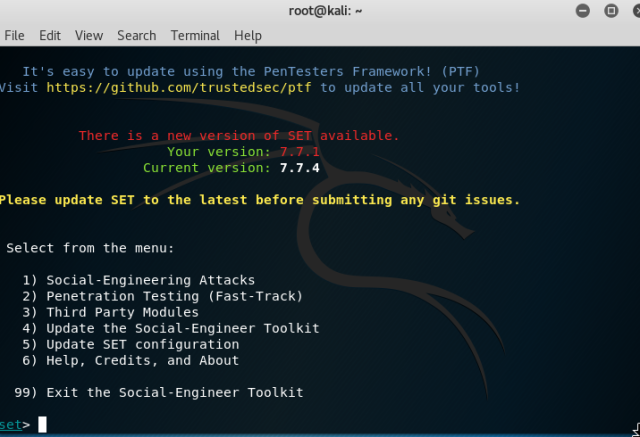
Select 1 (Social-Engineering Attacks) from the options.
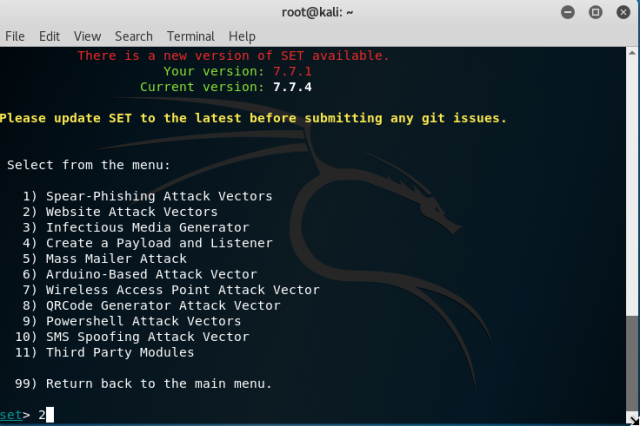
And after selecting “Website Attack Vectors” , choose “Credential Harvestor Attack Method”.
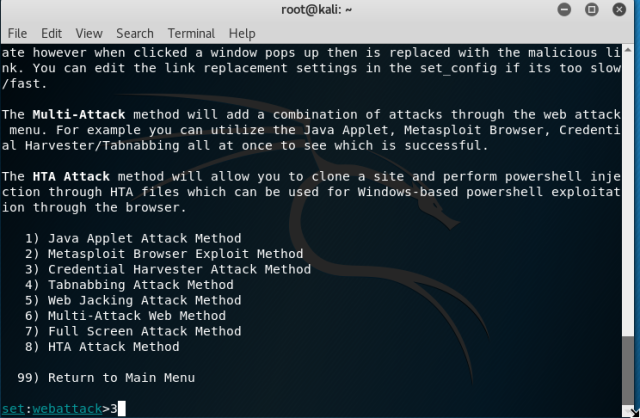
So, here you have a option – Web Template or Site Cloner. If you are planning to clone any of those from the facebook, gmail or yahoo, you can always go with the first or if you want to clone a different site then choose second option.
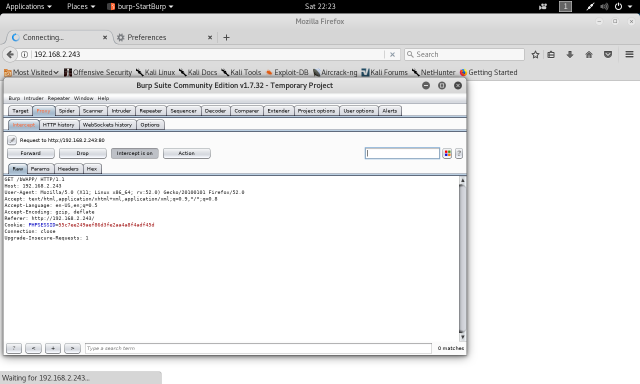
Before going any further, open another terminal and check the IP of your machine.
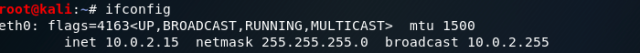
Enter your IP when asked and remember not to close your terminal.
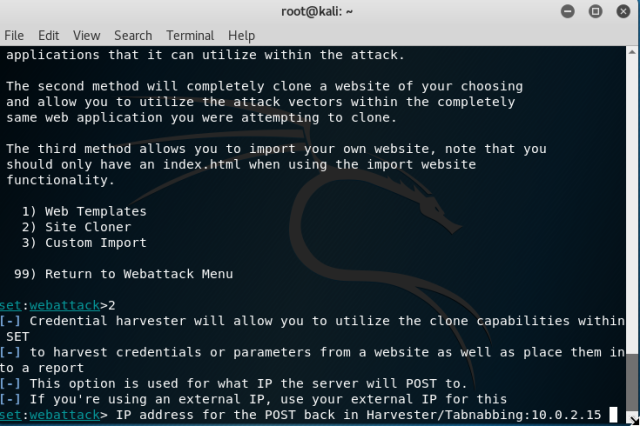
Go to browser and enter your IP, you can also change your IP to look like URL by using any of the tinyURL services available.
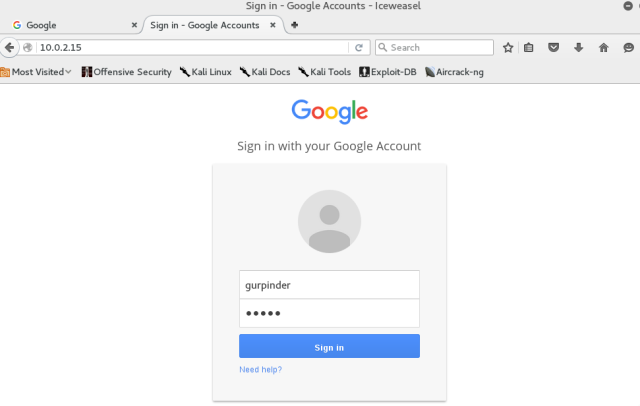
Wow! Now its a time to harvest those credentials. 🙂 Go to the directory – /var/www/html
Now, enter a command to list all the files in the directories.
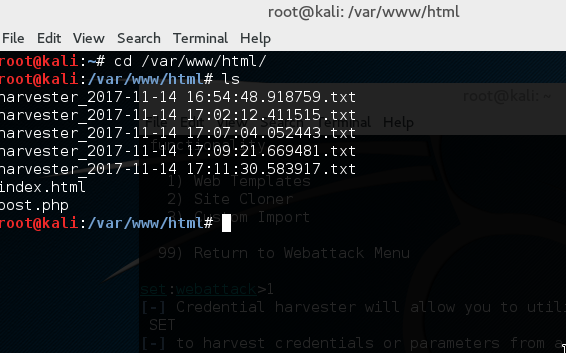
Copy the one that you want to see and enter the command below to display the contents of the file and here we go:
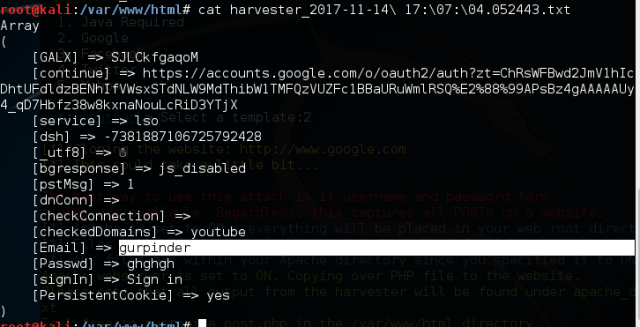
So, this was one of things you can do with this tool. To make it work over internet, you need to use your Public IP and port forward it over port 80. Enjoy your Hack and make sure not to use it for wrong purposes or you will be in trouble. 🙂